The Snort rule that is triggered is:
alert ip any any -> any any (msg:"GPL ATTACK\_RESPONSE id check returned root"; content:"uid=0|28|root|29|"; fast\_pattern:only; classtype:bad-unknown; sid:2100498; rev:8;)
This rule generates an alert if any IP address in the network receives data from an external source that contains content with text matching the pattern of uid=0(root). The alert contains the message GPL ATTACK_RESPONSE id check returned root. The ID of the Snort rule that was triggered is 2100498.
The highlighted line in the figure displays a Sguil alert that was generated by visiting the testmyids website. The Snort rule and the packet data for the content received from the testmyvids webpage is displayed in the lower right-hand area of the Sguil interface.
Sguil Console Showing Test Alert from Snort IDS
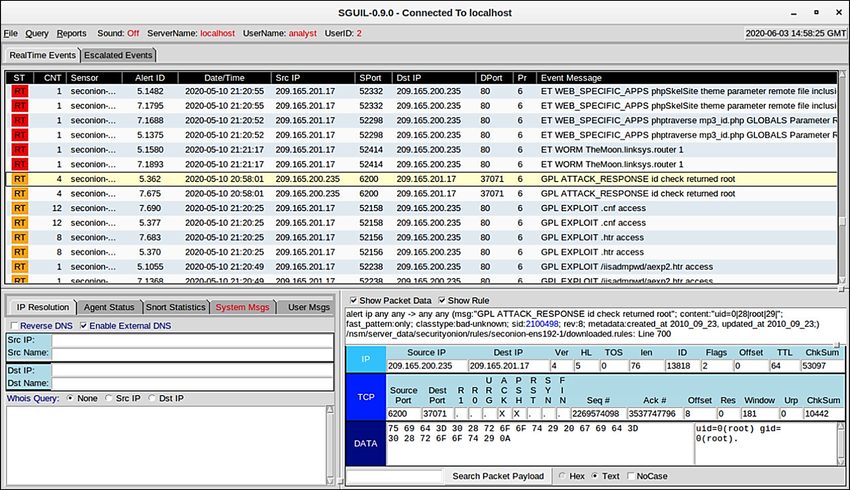
Session and Transaction Data
Zeek Session Data – Partial Contents
Transaction Data
Full Packet Captures
The figure illustrates the interface for the Network Analysis Monitor component of the Cisco Prime Infrastructure system, which, like Wireshark, can display full packet captures.
Cisco Prime Network Analysis Module – Full Packet Captur
Statistical Data
An example of an NSM tool that utilizes statistical analysis is Cisco Cognitive Threat Analytics.
Action Point
Get My 66 Page eBook on How to Run Success Ads ON TikTok for 2,000 Naira. Click Here to Buy.
Get my 90 Page ebook on How to Run Ads on Facebook. Click here to buy now.
P.S.: If you need private online training on any of the ICT courses I offer here and you are in Nigeria, please send me a DM on my WhatsApp at +2348103180831. Please note that the Training will be 100percent online. It will be delivered via Zoom or Google Meet.
PS: I know you might agree with some of the points raised in this article or disagree with some of the issues raised.
Please share your thoughts on the topic discussed. We would appreciate it if you could drop your comment. Thanks in anticipation.