The Common Vulnerability Scoring System (CVSS) is a risk assessment tool that is designed to convey the common attributes and severity of vulnerabilities in computer hardware and software systems. The third revision, CVSS 3.0, is a vendor-neutral, industry-standard, open framework for weighting the risks of a vulnerability using a variety of metrics. These weights combine to provide a score of the risk inherent in a vulnerability. The numeric score can be used to determine the urgency of the vulnerability, and the priority of addressing it. The benefits of the CVSS can be summarized as follows:
- It provides standardized vulnerability scores that should be meaningful across organizations.
- It provides an open framework with the meaning of each metric openly available to all users.
- It helps prioritize risk in a way that is meaningful to individual organizations.
The Forum of Incident Response and Security Teams (FIRST) has been designated as the custodian of the CVSS to promote it’s adoption globally. The Version 3 standard was developed with contributions by Cisco and other industry partners. Version 3.1 was released in June of 2019. The figure displays the specification page for the CVSS at the FIRST website.

CVSS Metric Groups
CVSS Metric Groups
CVSS Base Metric Group
| Criteria | Description |
|---|---|
| Attack vector | This is a metric that reflects the proximity of the threat actor to the vulnerable component. The more remote the threat actor is to the component, the higher the severity. Threat actors close to your network or inside your network are easier to detect and mitigate. |
| Attack complexity | This is a metric that expresses the number of components, software, hardware, or networks, that are beyond the attacker’s control and that must be present for a vulnerability to be successfully exploited. |
| Privileges required | This is a metric that captures the level of access that is required for a successful exploit of the vulnerability. |
| User interaction | This metric expresses the presence or absence of the requirement for user interaction for an exploit to be successful. |
| Scope | This metric expresses whether multiple authorities must be involved in an exploit. This is expressed as whether the initial authority changes to a second authority during the exploit. |
| Term | Description |
|---|---|
| Confidentiality Impact | This is a metric that measures the impact to confidentiality due to a successfully exploited vulnerability. Confidentiality refers to the limiting of access to only authorized users. |
| Integrity Impact | This is a metric that measures the impact on integrity due to a successfully exploited vulnerability. Integrity refers to the trustworthiness and authenticity of the information. |
| Availability Impact | This is a metric that measures the impact to availability due to a successfully exploited vulnerability. Availability refers to the accessibility of information and network resources. Attacks that consume network bandwidth, processor cycles, or disk space all impact the availability. |
The CVSS Process
A detailed user guide that defines metric criteria, examples of assessments of common vulnerabilities, and the relationship of metric values to the final score is available to support the process.
| Metric Name | Initials | Possible Values | Values |
|---|---|---|---|
| Attack Vector | AV | [N, A, L, P] | N = Network A = Adjacent L = Local P = Physical |
| Attack Complexity | AC | [L, H] | L = Low H = High |
| Privileges Required | PR | [N, L, H] | N = None L = Low H = High |
| User Interaction | UI | [N, R] | N = None R = Required |
| Scope | S | [U, C] | U = Unchanged C = Changed |
| Confidentiality Impact | C | [H, L, N] | H = High L = Low N = None |
| Integrity Impact | I | [H, L, N] | H = High L = Low N = None |
| Availability Impact | A | [H, L, N] | H = High L = Low N = None |
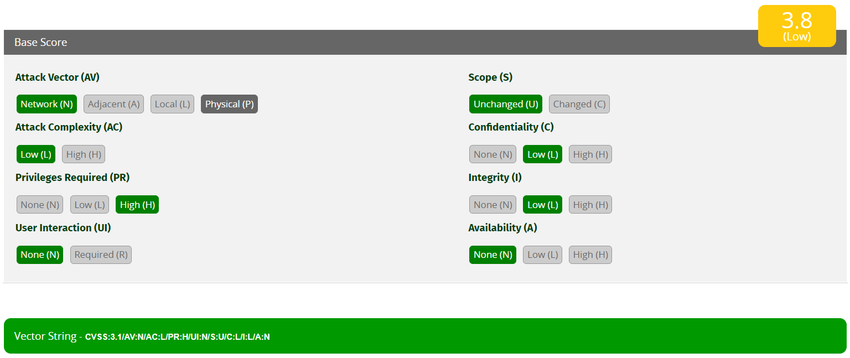
| Metric Name | Values |
|---|---|
| Attack Vector, AV | Network |
| Attack Complexity, AC | Low |
| Privileges Required, PR | High |
| User Interaction, UI | None |
| Scope, S | Unchanged |
| Confidentiality Impact, C | Low |
| Integrity Impact, I | Low |
| Availability Impact, A | None |
CVSS Reports
| Rating | CVSS Score |
|---|---|
| None | 0 |
| Low | 0.1 – 3.9 |
| Medium | 4.0 – 6.9 |
| High | 7.0 – 8.9 |
| Critical | 9.0 – 10.0 |
Frequently, the Base and Temporal metric group scores will be supplied to customers by the application or security vendor in whose product the vulnerability has been discovered. The affected organization completes the environmental metric group to tailor the vendor-supplied scoring to the local context.
The resulting score serves to guide the affected organization in the allocation of resources to address the vulnerability. The higher the severity rating, the greater the potential impact of an exploit and the greater the urgency in addressing the vulnerability. While not as precise as the numeric CVSS scores, the qualitative labels are very useful for communicating with stakeholders who are unable to relate to the numeric scores.
In general, any vulnerability that exceeds 3.9 should be addressed. The higher the rating level, the greater the urgency for remediation.
Other Vulnerability Information Sources
This is a dictionary of common names, in the form of CVE identifiers, for known cybersecurity vulnerabilities. The CVE identifier provides a standard way to research a reference to vulnerabilities. When a vulnerability has been identified, CVE identifiers can be used to access fixes. In addition, threat intelligence services use CVE identifiers, and they appear in various security system logs. The CVE Details website provides a linkage between CVSS scores and CVE information. It allows browsing of CVE vulnerability records by CVSS severity rating.

This utilizes CVE identifiers and supplies additional information on vulnerabilities such as CVSS threat scores, technical details, affected entities, and resources for further investigation. The database was created and is maintained by the U.S. government National Institute of Standards and Technology (NIST) agency.

PS: If you would like to have an online course on any of the courses that you found on this blog, I will be glad to do that on individual and corporate level, I will be very glad to do that I have trained several individuals and groups and they are doing well in their various fields of endeavour. Some of those that I have trained includes staffs of Dangote Refinery, FCMB, Zenith Bank, New Horizons Nigeria among others. Please come on Whatsapp and let’s talk about your training. You can reach me on Whatsapp HERE. Please note that I will be using Microsoft Team to facilitate the training.
I know you might agree with some of the points that I have raised in this article. You might not agree with some of the issues raised. Let me know your views about the topic discussed. We will appreciate it if you can drop your comment. Thanks in anticipation.
Fact Check Policy
CRMNIGERIA is committed to fact-checking in a fair, transparent and non-partisan manner. Therefore, if you’ve found an error in any of our reports, be it factual, editorial, or an outdated post, please contact us to tell us about it.
|


