Host Based Firewalls In Cybersecurity: The Facts

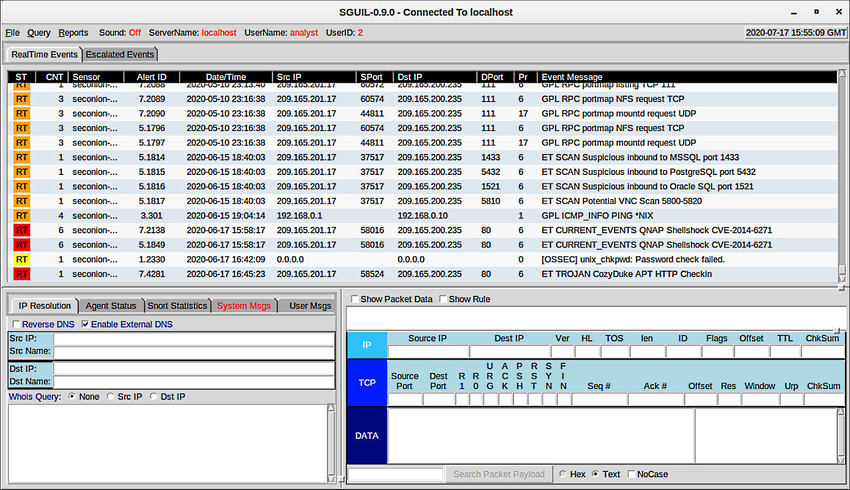
Host-based firewalls may use a set of predefined policies, or profiles, to control packets entering and leaving a computer. They also may have rules that can be directly modified or created to control access based on addresses, protocols, and ports. Host-based firewall applications can also be configured to issue alerts to users if suspicious behaviour is detected.
They can then offer the user the ability to allow an offending application to run or to be prevented from running in the future.
In addition, common activities such as DNS lookups and other routine events can show up in host-based firewall logs, so filtering and other parsing techniques are useful for inspecting large amounts of log data.
Whether installed completely on the host or distributed, host-based firewalls are an important layer of network security along with network-based firewalls. Here are some examples of host-based firewalls:
- Windows Defender Firewall – First included with Windows XP, Windows Firewall (now Windows Defender Firewall) uses a profile-based approach to firewall functionality. Access to public networks is assigned the restrictive Public firewall profile. The Private profile is for computers that are isolated from the internet by other security devices, such as a home router with firewall functionality. The Domain profile is the third available profile. It is chosen for connections to a trusted network, such as a business network that is assumed to have an adequate security infrastructure. Windows Firewall has logging functionality and can be centrally managed with customized group security policies from a management server such as System Center 2012 Configuration Manager.
- iptables – This is an application that allows Linux system administrators to configure network access rules that are part of the Linux kernel Netfilter modules.
- nftables – The successor to iptables, nftables is a Linux firewall application that uses a simple virtual machine in the Linux kernel. Code is executed within the virtual machine that inspects network packets and implements decision rules regarding packet acceptance and forwarding.
- TCP Wrappers – This is a rule-based access control and logging system for Linux. Packet filtering is based on IP addresses and network services.
Host-Based Intrusion Detection
A host-based intrusion detection system (HIDS) is designed to protect hosts against known and unknown malware.
A HIDS can perform detailed monitoring and report on the system configuration and application activity. It can provide log analysis, event correlation, integrity checking, policy enforcement, rootkit detection, and alerting. A HIDS will frequently include a management server endpoint, as shown in the figure.
A HIDS is a comprehensive security application that combines the functionalities of antimalware applications with firewall functionality. A HIDS not only detects malware but also can prevent it from executing if it should reach a host. Because the HIDS software must run directly on the host, it is considered an agent-based system.
Host-based Intrusion Detection Architecture
HIDS Operation
It can be said that host-based security systems function as both detection and prevention systems because they prevent known attacks and detect unknown potential attacks.
A HIDS uses both proactive and reactive strategies. A HIDS can prevent intrusion because it uses signatures to detect known malware and prevent it from infecting a system. However, this strategy is only good against known threats. Signatures are not effective against new, or zero-day, threats.
In addition, some malware families exhibit polymorphism. This means that variations of a type, or family, of malware, may be created by attackers that will evade signature-based detections by changing aspects of the malware signature just enough so that it will not be detected. An additional set of strategies are used to detect the possibility of successful intrusions by malware that evades signature detection:
- Anomaly-based – Host system behaviour is compared to a learned baseline model of normal behaviour. Significant deviations from the baseline are interpreted as the result of some sort of intrusion. If an intrusion is detected, the HIDS can log details of the intrusion, send alerts to security management systems, and take action to prevent the attack. The measured baseline is derived from both user and system behaviour. Because many things other than malware can cause system behaviour to change, anomaly detection can create many erroneous results which can increase the workload for security personnel and also lower the credibility of the system.
- Policy-based – Normal system behaviour is described by rules, or the violation of rules, that are predefined. Violation of these policies will result in action by the HIDS. The HIDS may attempt to shut down software processes that have violated the rules and can log these events and alert personnel to violations. Most HIDS software comes with a set of predefined rules. With some systems, administrators can create custom policies that can be distributed to hosts from a central policy management system.
HIDS Products
Action Point
PS: If you would like to have an online course on any of the courses that you found on this blog, I will be glad to do that on an individual and corporate level, I will be very glad to do that I have trained several individuals and groups and they are doing well in their various fields of endeavour. Some of those that I have trained includes staffs of Dangote Refinery, FCMB, Zenith Bank, New Horizons Nigeria among others. Please come on Whatsapp and let’s talk about your training. You can reach me on Whatsapp HERE. Please note that I will be using Microsoft Team to facilitate the training.
I know you might agree with some of the points that I have raised in this article. You might not agree with some of the issues raised. Let me know your views about the topic discussed. We will appreciate it if you can drop your comment. Thanks in anticipation.
Fact Check Policy
CRMNIGERIA is committed to fact-checking in a fair, transparent and non-partisan manner. Therefore, if you’ve found an error in any of our reports, be it factual, editorial, or an outdated post, please contact us to tell us about it.
|