
Highlighting Various Network Security Monitoring Tool
In this article, I want to look at common network security monitoring tools in cybersecurity. Follow me as we look at this together in this article.
Common tools that are used for network security monitoring include:
- Network protocol analyzers such as Wireshark and Tcpdump
- NetFlow
- Security Information and Event Management Systems (SIEM)
It is also common for security analysts to rely on log files and Simple Network Management Protocol (SNMP) for network behaviour discovery.
Practically all systems generate log files to record and communicate their operations. By closely monitoring log files, a security analyst can gather extremely valuable information.
SNMP allows analysts to request and receive information about the operation of network devices. It is another good tool for monitoring the behaviour of a network.
Security analysts must be familiar with all of these tools.
Common Network Security Monitoring Tools
Network Protocol Analyzers
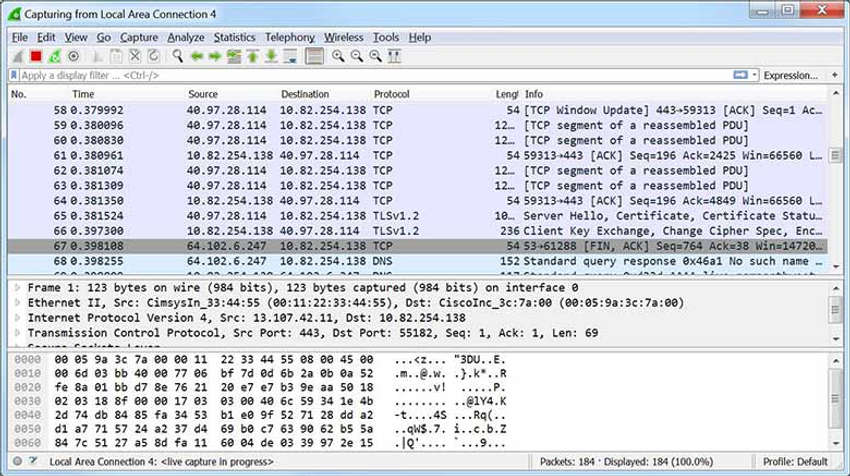
Wireshark can also open files that contain captured traffic from other software such as the tcpdump utility. Popular among UNIX-like systems such as Linux, tcpdump is a powerful utility with numerous command-line options. The example in the command output displays a sample tcpdump capture of ping packets.
[root@secOps analyst]# tcpdump -i hl-eth0 -n
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on hl-eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
10:42:19.841549 IP 10.0.0.12 > 10.0.0.11: ICMP echo request, id 2279, seq 5, length 64
10:42:19.841570 IP 10.0.0.11 > 10.0.0.12: ICMP echo reply, id 2279, seq 5, length 64
10:42:19.854287 IP 10.0.0.12 > 10.0.0.11: ICMP echo request, id 2279, seq 6, length 64
10:42:19.854304 IP 10.0.0.11 > 10.0.0.12: ICMP echo reply, id 2279, seq 6, length 64
10:42:19.867446 IP 10.0.0.12 > 10.0.0.11: ICMP echo request, id 2279, seq 7, length 64
10:42:19.867468 IP 10.0.0.11 > 10.0.0.12: ICMP echo reply, id 2279, seq 7, length 64
^C
6 packets captured
6 packets received by filter
0 packets dropped by kernel
[root@secOps analyst]#
NetFlow
This information includes the source and destination device IP information, the time of the communication, and the amount of data transferred. NetFlow does not capture the actual content on the flow. NetFlow functionality is often compared to a telephone bill. The bill identifies the destination number, the time and the duration of the call. However, it does not display the content of the telephone conversation.
NetFlow in the Network
For example, Cisco Stealthwatch collects NetFlow statistics to perform advanced functions including:
- Flow stitching – It groups individual entries into flows.
- Flow deduplication – It filters duplicate incoming entries from multiple NetFlow clients.
- NAT stitching – It simplifies flows with NAT entries.
There is a Cisco Stealthwatch channel on YouTube that provides many details about Stealthwatch and its uses.
SIEM and SOAR
Network security analysts must quickly and accurately assess the significance of any security event and answer the following critical questions:
- Who is associated with this event?
- Does the user have access to other sensitive resources?
- Does this event represent a potential compliance issue?
- Does the user have access to intellectual property or sensitive information?
- Is the user authorized to access that resource?
To help answer these questions, security analysts use:
- Security Information Event Management (SIEM)
- Security orchestration, automation, and response (SOAR)
SIEM Systems
In this course, we will use an open-source product called Security Onion that includes the ELK suite for SIEM functionality. ELK is an acronym for three products from Elastic:
- Elasticsearch – Document-oriented full-text search engine
- Logstash – Pipeline processing system that connects “inputs” to “outputs” with optional “filters” in-between
- Kibana – Browser-based analytics and search dashboard for Elasticsearch
Search the internet to learn more about Elastic. co and its suite of products.
Action Point
PS: If you would like to have an online course on any of the courses that you found on this blog, I will be glad to do that on an individual and corporate level, I will be very glad to do that because I have trained several individuals and groups and they are doing well in their various fields of endeavour. Some of those that I have trained include staff of Dangote Refinery, FCMB, Zenith Bank, and New Horizons Nigeria among others. Please come on Whatsapp and let’s talk about your training. You can reach me on Whatsapp HERE. Please note that I will be using Microsoft Team to facilitate the training.
I know you might agree with some of the points that I have raised in this article. You might not agree with some of the issues raised. Let me know your views about the topic discussed. We will appreciate it if you can drop your comment. Thanks in anticipation.
Fact Check Policy
CRMNIGERIA is committed to fact-checking in a fair, transparent and non-partisan manner. Therefore, if you’ve found an error in any of our reports, be it factual, editorial, or an outdated post, please contact us to tell us about it.
|










Leave a Reply